Hi all, I was trying to for some time automatically unencrypt my LUKS partition on boot so I wasn´t stopped by the password prompt on boot. Usually I turn on my PC and go do something else while it boots (it takes less than 10 seconds, but still old habits die hard). It was a bit frustrating when I cam back and the LUKS password prompt was there instead my display manager.
I use encryption o my drive just as as safeguard when discarding it or if it fails and I have to RMA. This grantees if someone has access to my drives but not my whole PC, they can´t acess my data. I don´t recommend this if you are using a Laptop or your concern is having the whole PC stolen!
My goal was to have something similar to Bitlocker but still mantain control over my system. The main source for this tutorial is the Arch Wiki but focused on CachyOS.
ATTENTION: BACKUP YOUR DATA
The process is easy but any misstep potentially brick your bootloader.
I had a hard time making my crypttab.initramfs correct and had to use a rescue boot to save my PC.
The TLDR:
- Make sure you have Secure Boot enable and working
- Make sure you have TPM2 support running :
systemd-analyze has-tpm2
- Make a copy of your /etc/crypttab to /etc/crypttab.initramfs:
sudo cp /etc/crypttab /etc/cryptab.initramfs
- Enroll the PCR keys on the TPM2 slot of systemd-crypt
sudo systemd-cryptenroll --wipe-slot tpm2 --tpm2-device auto --tpm2-pcrs “1+3+5+7+11+12+14+15” /dev/nvmeXnXpX
Where /dev/nvmeXnXpX is your encypted device with system
- Change your HOOKS on /etc/mkinitcpio.conf:
sudo micro /etc/mkinitcpio.conf
Edit the line
HOOKS=(base udev autodetect microcode kms modconf block keyboard keymap consolefont plymouth encrypt filesystems)
to
HOOKS=(base systemd plymouth autodetect microcode modconf kms keyboard sd-vconsole sd-encrypt block filesystems fsck)
- Rebuild your initramfs with:
sudo mkinitcpio -P
- Reboot the PC and pray
The full Guide:
- Eneable Secure Boot
Cachy Wiki has an excellent guide on how to enable Secure Boot post installation.
Also make sure you have a TPM2 device available running:
systemd-analyze has-tpm2
Double check on Octopi if the package tpm2-tss is installed.
- Create the /etc/crypttab.initramfs file
As we are unlocking the device on boot time, we must identify it on /etc/crypttab.initramfs. This indicates the boot loader the device name (map), its UUID and how to unlock it (in our case, tpm2-auto). If you have only one encrypted drive, the easiest way to create the file is to copy the userspace version /etc/crypttab to /etc/crypttab.initramfs using the command:
sudo cp /etc/crypttab /etc/cryptab.initramfs
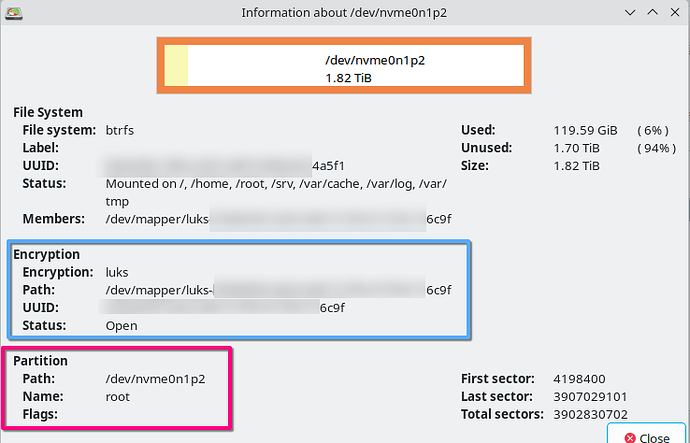
If you have more encrypted devices and they are on the userspace /etc/crypttab, you can do the same but edit out to leave only the root partition on the file. To check your your root partition name and UUID you can use gParted or other partitioning tool. use the ENCRYPTION section data, not the File System section!
Crypttab file has the format:
<name> <device> <password> <options>
- Name must be your mapper name. In this case luks-XXXXXXXXXXXX6c9f
- Device is UUID. In this case, XXXXXXXXXXXX6c9f or the name without “luks-”
- Password must be
noneto force use the TPM2 key
Once done you are ready ton enroll the TPM2 keys
- Enrolling the TPM2 keys and PCRs:
Arch Wiki has a great article about this step.
For this tutorial we will use the PCRs: “1+3+5+7+11+12+14+15”.
Bitlocker uses “0+2+4+8+9+10+11” for comparison. It is up to you judge your needs, but my rational is:
- “1+7” should be the absolute minimal. It requires password if hardware changes (1) or Secure Boot is disabled (7).
- Based on this forum post on [GUIDE] Setup TPM2 Autodecrypt - Linux - Framework Community, I agree with all omissions and additions. Quoted direct from the autor:
Here are the reasons for my config:
- I omitted 9 (Linux Kernel and grub), which requires rebuild every time there is a kernel update. As Fedora updates the Kernel quite often, I omitted this integrity check.
- I omitted 4 because I observed a change in its signature after a kernel update. I am assuming it will sometimes be changed by an regular update.
- I omitted 0 (firmware) and 2 (pluggable hardware), because it is explicitly recommended against bysystemd-cryptenroll man page
- I added 11 (ELF kernel image, embedded initrd and other payload of the PE image ) and 14 (shim) because 7, 11, 14 is recommended by systemd-cryptenroll man page
- I added 12 (kernel-config) because I don’t typically change kernel parameters
- I added 15 (volume key of activated LUKS volumes), because I don’t imagine I would change the LUKS volumes.
PCRs 12 and 15 are the most "personal"and should be considered case by case.
After deciding the PCRs, check the name of your root partition (based on gparted example, mine is /dev/nvme0n1p2. The comand to enroll the TPM keys is:
sudo systemd-cryptenroll --wipe-slot tpm2 --tpm2-device auto --tpm2-pcrs “1+3+5+7+11+12+14+15” /dev/nvmeXnXpX
If any of the PCRs changes you just neede to rerun the previous command to update your TPM2 key.
Once done, you are ready to modify the initramfs with the new information.
- Updating the initramfs
The boot hooks must be changed to include the necessary systemd hooks to auto unlock your LUKS partition. To do so, firt we have to change the /etc/mkinitcpio.conf file.
Make a backup copy of the original file as I bricked my system multiple times here.
sudo cp /etc/mkinitcpio.conf /etc/mkinitcpio.conf.old
When ready, open the original file with a text editor and find the line:
HOOKS=(base udev autodetect microcode kms modconf block keyboard keymap consolefont plymouth encrypt filesystems)
change to
HOOKS=(base systemd plymouth autodetect microcode modconf kms keyboard sd-vconsole sd-encrypt block filesystems fsck)
fsck is optional, plymouth must be changed to run just after systemd
Once done, rebuid your initramfs and rebboot the system.
sudo mkinitcpio -P
On the next boot, everything should be exactly the same, but you won´t be prompted to type your LUKS password.
I recommend you also make a recovery key for your LUKS partition.
Follow this Arch Wiki link (section 4) systemd-cryptenroll - ArchWiki.
Please let me know if the tutotrial works for you or if something neede to be adjusted.
Currently I can only add 2 links to the post. When this restrictions is lifted I will format with more sources.